Capability-driven framework to automate discovery of bounded contexts in large-scale requirements engineering
- Faculty of Computer Engineering, Najafabad Branch, Islamic Azad University, Najafabad, Iran AND Big Data Research Center, Najafabad Branch, Islamic Azad University, Najafabad, Iran
- Department of Computer Engineering, Abadan Branch, Islamic Azad University, Abadan, Iran

Received: 2024-06-15
Revised: 2024-07-20
Accepted: 2024-08-01
Published in Issue 2024-12-15

This work is licensed under a Creative Commons Attribution 4.0 International License.
How to Cite
PDF views: 363
HTML views: 16
Abstract
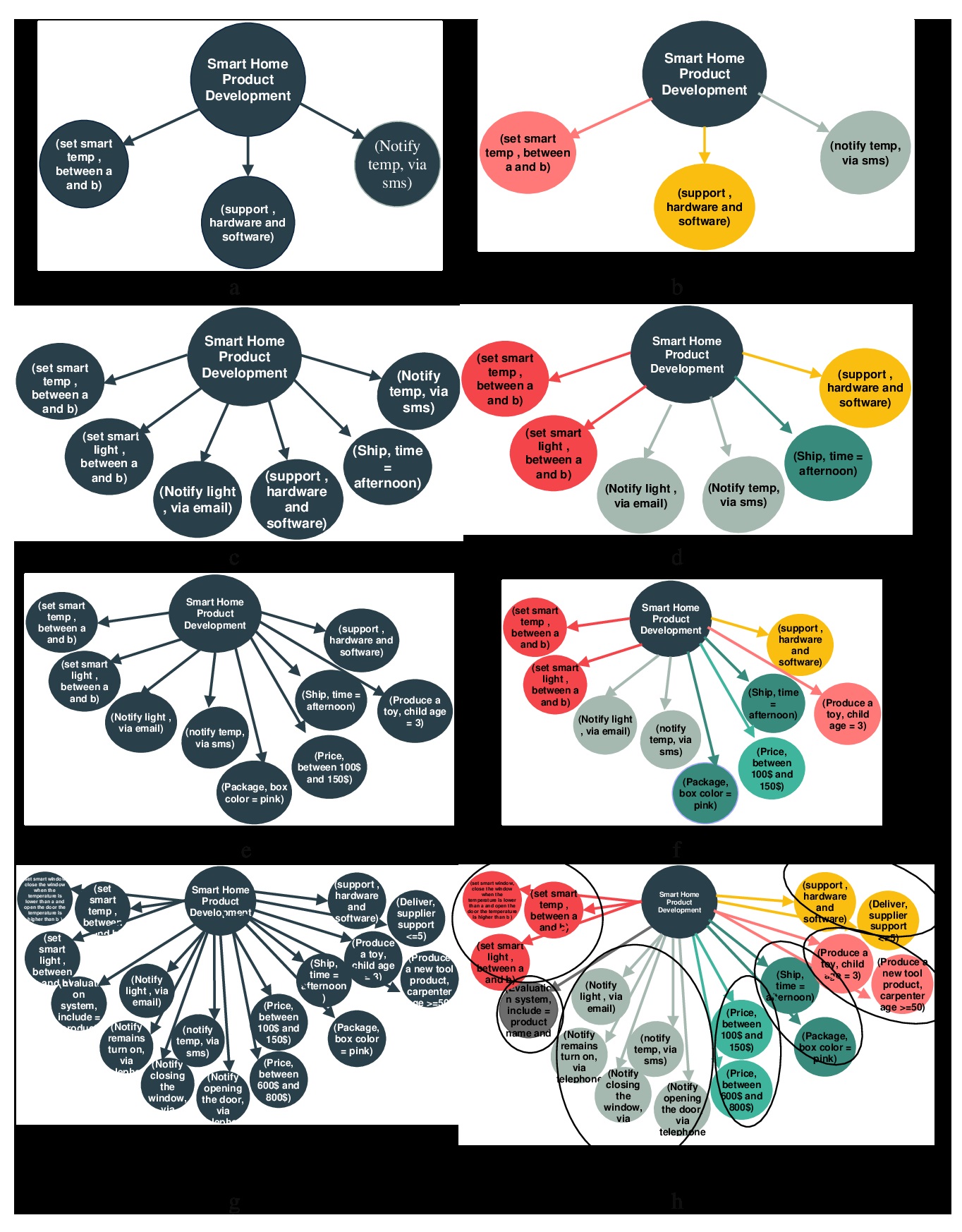
Large-scale requirement engineering needs automated precise and efficient capability modeling and analyzing methods formally to interoperate with the evolving and goal-driven requirements. The proposed capability-driven requirement engineering framework presents a two-layer framework for the automation of requirements engineering. In the first layer, a meta-model is proposed to define a fault-free model instantiating the requirements model, and thereby ensuring consistency in the
process of requirement execution and in the second layer the analysis algorithms are provided for discovering and querying the boundaries and capabilities of the system at the abstract level. The proposed capability-driven requirement framework offers the ability to specify, decompose, and identify the requirement traces to execute the activities regarding available capacities and resources. We also provide the applicability of the approach from various points of view including quality and stability of bounded contexts, average precision, and query assessment. As a running example, we highlight the essential role of electrical features in achieving seamless integration and operation, encompassing power distribution, automation systems, energy efficiency, and safety measures. The proposed capability-driven requirement framework is crucial for effective smart home engineering
in this context. The proposed structured, formal description of software requirement capabilities may increase the precision and recall of module discovery mechanisms for large-scale software engineering. An average precision of more than 93% is a significant achievement in the context of information retrieval and evaluation.
Keywords
- Requirement engineering,
- Smart Home,
- Software capability,
- Bounded context,
- Capability querying
References
- P. Loucopoulos and V. Karakostas, "System requirements engineering", McGraw-Hill, Inc., 1995.
- G. Kotonya and I. Sommerville, "Requirements engineering: processes and techniques" Wiley Publishing, 1998.
- I. Sommerville, "Software engineering", 9th Edition,"ISBN-10137035152, 2011.
- P. Loucopoulos and E. Kavakli, "Enterprise modelling and the teleological approach to requirements engineering," International Journal of Cooperative Information Systems, vol. 4, no. 01, pp. 45-79, 1995. https://doi.org/10.1142/s0218843095000032
- A. Van Lamsweerde, "Requirements engineering: From system goals to UML models to software", Chichester, UK: John Wiley & Sons, 2009. https://doi.org/10.1109/icse.2003.1201266
- J. Siddiqi, "Requirement engineering: The emerging wisdom", IEEE Software, no. 2, p. 15, 1996. https://doi.org/10.1109/ms.1996.506458
- Abadeh, Maryam Nooraei. "Knowledge-enhanced software refinement: leveraging reinforcement learning for search-based quality engineering." Automated Software Engineering 31, no. 2 (2024): 57. https://doi.org/10.1007/s10515-024-00456-7.
- S. Bērziša et al., "Capability driven development: an approach to designing digital enterprises", Business & Information Systems Engineering, vol. 57, no. 1, pp. 15-25, 2015. https://doi.org/10.1007/978-3-319-90424-5_13
- M. H. Danesh, P. Loucopoulos, and E. Yu, "Dynamic capabilities for sustainable enterprise IT–a modeling framework", International Conference on Conceptual Modeling, 2015, pp. 358-366: Springer. https://doi.org/10.1007/978-3-319-25264-3_26
- P. Loucopoulos, C. Stratigaki, M. H. Danesh, G. Bravos, D. Anagnostopoulos, and G. Dimitrakopoulos, "Enterprise capability modeling: concepts, method, and application", 2015 International Conference on Enterprise Systems (ES), 2015, pp. 66-77: IEEE. https://doi.org/10.1109/es.2015.14
- P. Oaks, A. H. Ter Hofstede, and D. Edmond, "Capabilities: Describing what services can do", International Conference on Service-Oriented Computing, 2003, pp. 1-16: Springer. https://doi.org/10.1007/978-3-540-24593-3_1
- I.-s. Standards Board, "IEEE Recommended Practice for Software Requirements Specications", IEEE Standard 830, 04/09 2000. https://doi.org/10.1109/ieeestd.1998.88286
- R. S. Wahono, "Analyzing requirements engineering problems", IECI Japan Workshop, 2003.
- M. Hause, "The SysML modelling language", Fifteenth European Systems Engineering Conference, 2006, vol. 9, pp. 1-12: Citeseer. https://doi.org/10.1049/ic:20050131
- P. H. Feiler, D. P. Gluch, and J. J. Hudak, "The architecture analysis & design language (AADL): An introduction", Carnegie-Mellon Univ Pittsburgh PA Software Engineering Inst2006. https://doi.org/10.21236/ada455842
- O. MARTE, "UML profile for modeling and analysis of real-time and embedded systems (MARTE)", ed: OMG, 2011. https://doi.org/10.1016/c2012-0-13536-5
- B. SISO, "Guide for Base Object Model (BOM) Use and Implementation. SISO", SISO-STD-003.02006.
- S. Bernardi, J. Merseguer, and D. C. Petriu, "Model-driven dependability assessment of software systems", Springer, 2013. https://doi.org/10.1007/978-3-642-39512-3
- B. Mohit, "Named entity recognition", Natural language processing of semitic languages: Springer, 2014, pp. 221-245. https://doi.org/10.1007/978-3-642-45358-8_7
- E. Brill, "A simple rule-based part of speech tagger", Proceedings of the third conference on Applied natural language processing, 1992, pp. 152-155: Association for Computational Linguistics. https://doi.org/10.3115/1075527.1075553
- I. K. Raharjana, D. Siahaan, and C. Fatichah, "User story extraction from online news for software requirements elicitation: A conceptual model", 16th International Joint Conference on Computer Science and Software Engineering (JCSSE), 2019, pp. 342-347: IEEE. https://doi.org/10.1109/jcsse.2019.8864199
- R. M. Fano, "Transmission of information: A statistical theory of communications", American Journal of Physics, vol. 29, no. 11, pp. 793-794, 1961. https://doi.org/10.1119/1.1937609
- J. A. Bullinaria and J. P. Levy, "Extracting semantic representations from word co-occurrence statistics: A computational study", Behavior research methods, vol. 39, no. 3, pp. 510-526, 2007. https://doi.org/10.3758/bf03193020
- Y. Tian, D. Lo, and J. Lawall, "Automated construction of a software-specific word similarity database", Software Evolution Week-IEEE Conference on Software Maintenance, Reengineering, and Reverse Engineering (CSMR-WCRE), 2014, pp. 44-53: IEEE. https://doi.org/10.1109/csmr-wcre.2014.6747213
- M. Ester, H.-P. Kriegel, J. Sander, M. Wimmer, and X. Xu, "Incremental clustering for mining in a data ware housing", University of Munich Oettingenstr, vol. 67.
- A. M. Bakr, N. M. Ghanem, and M. A. Ismail, "Efficient incremental density-based algorithm for clustering large datasets", Alexandria Engineering Journal, vol. 54, no. 4, pp. 1147-1154, 2015. https://doi.org/10.1016/j.aej.2015.08.009
- J. Han, M. Kamber, and J. Pei, "Data Mining: Concepts and Techniques", Morgan Kauffman, 2011. https://doi.org/10.1109/icmira.2013.45
- A. K. Jain and J. Moreau, "Bootstrap technique in cluster analysis", Pattern Recognition, vol. 20, no. 5, pp. 547-568, 1987. https://doi.org/10.1016/0031-3203(87)90081-1
- R.-H. Li, L. Qin, J. X. Yu, and R. Mao, "Influential community search in large networks", Proceedings of the VLDB Endowment, vol. 8, no. 5, pp. 509-520, 2015. https://doi.org/10.14778/2735479.2735484
- R. L. Rosnow and R. Rosenthal, "The volunteer subject revisited", Australian Journal of Psychology, vol. 28, no. 2, pp. 97-108, 1976. https://doi.org/10.1080/00049537608255268
- A. Van Lamsweerde, et al., "The KAOS project: Knowledge acquisition in automated specification of software" in Proc. of the AAAI Spring Symposium Series, Design of Composite Systems, 1991, 1991, pp. 59-62.
- H. Kaiya, H. Horai, and M. Saeki, "AGORA: Attributed goal-oriented requirements analysis method", Proceedings IEEE joint international conference on requirements engineering, 2002, pp. 13-22: Ieee. https://doi.org/10.1109/icre.2002.1048501
- Ghaedi Heidari, Saeedeh, and Shohreh Ajoudanian. "Automatic pattern-based consistency checking in model refactoring: introducing a formal behavioral preserving method." Innovations in Systems and Software Engineering 20, no. 1 (2024): 65-84. https://doi.org/10.1007/s11334-022-00525-8
- A. Afrin and M. Sadiq, "An integrated approach for the selection of software requirements using fuzzy AHP and fuzzy TOPSIS method", in 2017 International Conference on Intelligent Computing, Instrumentation and Control Technologies (ICICICT), 2017, pp. 1094-1100: IEEE. https://doi.org/10.1109/icicict1.2017.8342722
- M. Sadiq and S. Nazneen, "Elicitation of software testing requirements from the selected set of software's requirements in GOREP", International Journal of Computational Systems Engineering, vol. 5, no. 3, pp. 152-160, 2019. https://doi.org/10.1504/ijcsyse.2019.10022447
- S. Khan, C. W. Mohammad, and M. Sadiq, "Generating Patterns and Sub-Patterns of Pairwise Comparison Matrices for the Selection of Software Requirements", International Conference on Advances in Computing, Communication Control and Networking (ICACCCN), 2018, pp. 91-97: IEEE. https://doi.org/10.1109/icacccn.2018.8748860
- Nooraei Abadeh, Maryam, and Mansooreh Mirzaie. "DiffPageRank: an efficient differential PageRank approach in MapReduce." The Journal of Supercomputing 77, no. 1 (2021): 188-211. https://doi.org/10.1007/s11227-020-03265-3
- M. Sadiq, T. Hassan, and S. Nazneen, "AHP_GORE_PSR: Applying analytic hierarchy process in goal oriented requirements elicitation method for the prioritization of software requirements", 3rd International Conference on Computational Intelligence & Communication Technology (CICT), 2017, pp. 1-5: IEEE. https://doi.org/10.1109/ciact.2017.7977366
- A. Mahmoud and G. Williams, "Detecting, classifying, and tracing non-functional software requirements", Requirements Engineering, vol. 21, no. 3, pp. 357-381, 2016. https://doi.org/10.1007/s00766-016-0252-8
- L. Zhao et al., "Natural Language Processing (NLP) for Requirements Engineering: A Systematic Mapping Study", arXiv preprint arXiv:2004.01099, 2020. 10.48550/arXiv.2004.01099
- H. Meth, B. Mueller, and A. Maedche, "Designing a requirement mining system", Journal of the Association for Information Systems, vol. 16, no. 9, p. 799, 2015. 10.17705/1jais.00408
- R. Pinquié, P. Véron, F. Segonds, and N. Croué, "Natural Language Processing of Requirements for Model-Based Product Design with ENOVIA/CATIA V6", IFIP International Conference on Product Lifecycle Management, 2015, pp. 205-215: Springer. https://doi.org/10.1007/978-3-319-33111-9_19
- P. Saint-Dizier, "Mining incoherent requirements in technical specifications: Analysis and implementation", Data & Knowledge Engineering, vol. 117, pp. 290-306, 2018. https://doi.org/10.1016/j.datak.2018.05.006
- D. Janssens, "Natural Language Processing in Requirements Elicitation and Requirements Analysis: a Systematic Literature Review", ACM Computing Surveys, Volume 54, Issue 3, 2019.
- C. Arora, M. Sabetzadeh, L. Briand, and F. Zimmer, "Extracting domain models from natural-language requirements: approach and industrial evaluation" Proceedings of the ACM/IEEE 19th International Conference on Model Driven Engineering Languages and Systems, 2016, pp. 250-260. https://doi.org/10.1145/2976767.2976769
- C. Arora, M. Sabetzadeh, and L. C. Briand, "An empirical study on the potential usefulness of domain models for completeness checking of requirements", Empirical Software Engineering, vol. 24, no. 4, pp. 2509-2539, 2019. https://doi.org/10.1007/s10664-019-09693-x
- Sadeghi, Hajar, and Shohreh Ajoudanian. "Optimized feature selection in software product lines using discrete bat algorithm." International Journal of Computational Intelligence and Applications, vol 21, no 1, 2022. https://doi.org/10.1142/s1469026822500031
- K. Karlapalem, H. P. Yeung, and P. C. Hung, "CapBasED-AMS-A Framework for Capability-Based and Event-Driven Activity Management System", CoopIS, 1995, vol. 95, pp. 205-219.
- W. Derguech and S. Bhiri, "Modelling, interlinking and discovering capabilities", ACS International Conference on Computer Systems and Applications (AICCSA), 2013, pp. 1-8: IEEE.
- https://doi.org/10.1109/aiccsa.2013.6616444
- S. Bhiri, W. Derguech, and M. Zaremba, "Modelling capabilities as attribute-featured entities", International Conference on Web Information Systems and Technologies, 2012, pp. 70-85: Springer. https://doi.org/10.1007/978-3-642-36608-6_5
- W. Derguech, S. Bhiri, S. Hasan, and E. Curry, "Using formal concept analysis for organizing and discovering sensor capabilities", The Computer Journal, vol. 58, no. 3, pp. 356-367, 2015. https://doi.org/10.1093/comjnl/bxu088
- IEEE Standard Glossary of Software Engineering Terminology, in IEEE Std 610.12-1990 , pp.1-84, 31 Dec. 1990, doi: 10.1109/IEEESTD.1990.101064.
- Sejin Jung, Junbeom Yoo, Sam Malek, “A systematic co-engineering of safety and security analysis in requirements engineering process”, International Journal of Critical Infrastructure Protection, Volume 43, 2023, https://doi.org/10.1016/j.ijcip.2023.100642
- Rademacher, F., Sachweh, S., Zündorf, A. “A Modeling Method for Systematic Architecture Reconstruction of Microservice-Based Software Systems”, Lecture Notes in Business Information Processing, vol 387. Springer, Cham. 2020. https://doi.org/10.1007/978-3-030-49418-6_21
- Siti Rochimah, & Bintang Nuralamsyah. “Decomposing Monolithic to Microservices: Keyword Extraction and BFS Combination Method to Cluster Monolithic’s Classes”, Jurnal RESTI 7(2), 263- 270. 2023. https://doi.org/10.29207/resti.v7i2.4866
- G. Filippone, N. Qaisar Mehmood, M. Autili, F. Rossi and M. Tivoli, "From monolithic to microservice architecture: an automated approach based on graph clustering and combinatorial optimization", 2023 IEEE 20th International Conference on Software Architecture (ICSA), L'Aquila, Italy, 2023, pp. 47-57, doi: 10.1109/ICSA56044.2023.00013.
- Kudo, T.N., Bulcão-Neto, R.d.F., Neto, V.V.G. et al. “Aligning requirements and testing through metamodeling and patterns: design and evaluation”, Requirements Eng 28, 97–115, 2023, https://doi.org/10.1007/s00766-022-00377-5
- J. Dąbrowski, E. Letier, A. Perini, and A. Susi, "Mining and searching app reviews for requirements engineering: Evaluation and replication studies", Information Systems, vol. 114, p. 102181, 2023/03/01/ 2023. https://doi.org/10.1016/j.is.2023.102181
- T. Cardona, E. A. Cudney, R. Hoerl, and J. Snyder, "Data Mining and Machine Learning Retention Models in Higher Education", Journal of College Student Retention: Research, Theory & Practice, vol. 25, no. 1, pp. 51-75, 2023. https://doi.org/10.1177/1521025120964920
- L. Wijerathna, A. Aleti, T. Bi, and A. Tang, "Mining and relating design contexts and design patterns from Stack Overflow", Empirical Software Engineering, vol. 27, no. 1, p. 8, 2021/10/23. https://doi.org/10.1007/s10664-021-10034-0
- P. Sangaroonsilp, H. K. Dam, M. Choetkiertikul, C. Ragkhitwetsagul, and A. Ghose, "A taxonomy for mining and classifying privacy requirements in issue reports", Information and Software Technology, vol. 157, p. 107162, 2023. https://doi.org/10.1016/j.infsof.2023.107162
- W. Abdeen, X. Chen and M. Unterkalmsteiner, "An approach for performance requirements verification and test environments generation", Requirements Engineering, vol. 28, no. 1, pp. 117-144, 2023. https://doi.org/10.1007/s00766-022-00379-3

 10.57647/j.mjee.2024.1804.50
10.57647/j.mjee.2024.1804.50